By Rachel Kim
A few weeks ago on, March 31, David Shaw, UCLA’s Chief Information Security Officer, reported to the Bruin community of a cybersecurity attack involving government agencies, private companies, and universities—including UCLA.
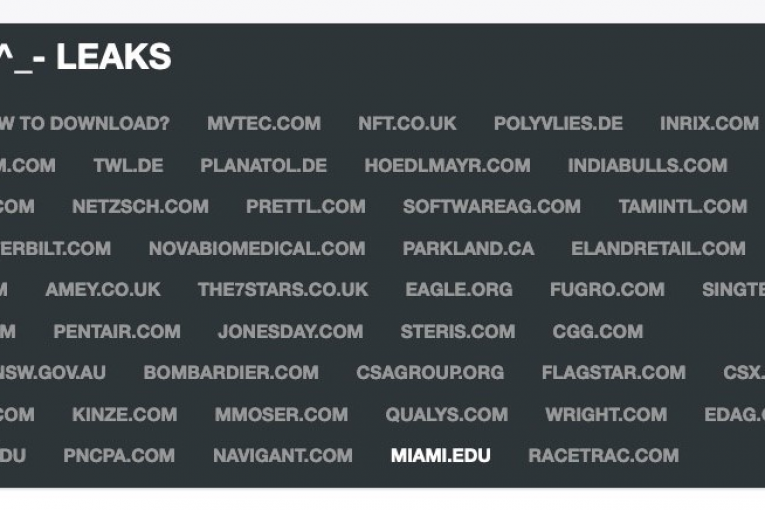
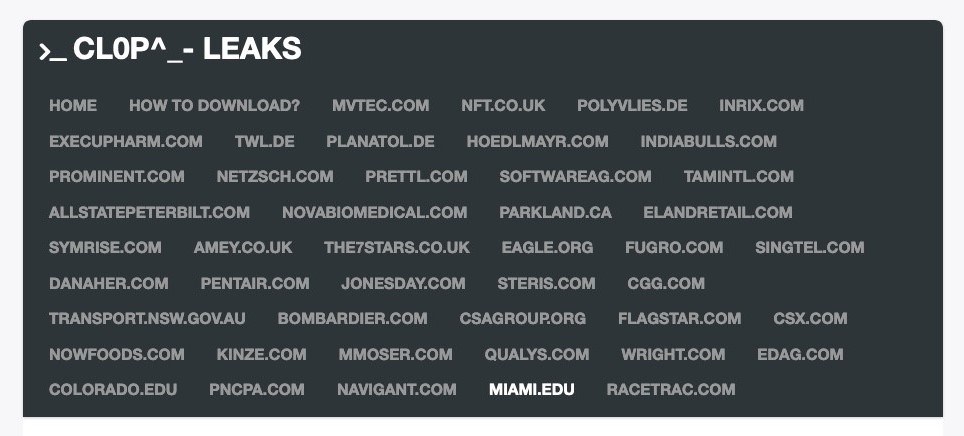
According to Gizmodo, “As of Thursday [April 1], at least six different universities have allegedly had their data leaked to the dark web.” The known schools include: the University of California system, Stanford University’s School of Medicine, the University of Colorado, the University of Miami, Yeshiva University, and the University of Maryland, Baltimore. It was said that sensitive information within the universities’ system had been copied and transferred by an unauthorized individual through the exploitation of Accellion, a file-transfer service.
Accellion specializes in securing file transmission and claims to “prevent breaches and compliance violations with total visibility and control over IP, PII, PHI and all sensitive content exchanged with third parties.”
According to their website, the enterprise’s firewall “simplifies complex infrastructure and reduces costs, while improving the user experience. When employees click the Accellion button, they know it’s the safe, secure way to share sensitive information with the outside world.” 
Accellion is said to have protected more than 25 million users over the past 20 years with over 3,000 organizations cooperating with the business.
However, back in December 2020, Accellion was a part of the zero-day exploit. A zero-day exploit is a cyber attack that occurs on the same day a vulnerability is located in software. During this time, only the hacker is aware of the weakness which makes the threat incredibly dangerous as the software can be exploited before the original creator is even aware of the threat. Cybercriminals exploited Accellion’s vulnerability in late 2020 and then again in January.
CL0P, a ransomware group, has published the stolen information from their Accellion breach on the dark web with some organizations claiming to have seen over 50 folders of data published in installments if they refuse to pay the ransom.
Emsisoft’s threat analyst, Brett Callow, said it is unlikely that CL0P has more data from other Accellion hacks.
“Whether CL0P is responsible for the hacks or is simply handling the extortion is impossible to say, but I suspect the latter,” Callow said. “Organizations in this position are without good options. If they don’t pay the ransom demand, their data will be released online in a series of installments. If they do pay, they’ll simply receive a pinky promise that the stolen data will be destroyed. Obviously, there is absolutely no reason to believe that the criminals would actually do this, especially if the data has significant market value.”
Similarly, the UC stated, “The attackers are threatening to publish, or have published, stolen information on the dark web in an attempt to extort organizations and individuals.”
Although we do not know the extent of the attack, it is believed that the stolen information includes, but is not limited to names, addresses, telephone numbers, birth dates, Social Security numbers, bank account information, and employment contracts.
Nonetheless, in an online statement posted in the beginning of March, the CEO of Accellion, Jonathan Yaron, said that Accellion has fixed all its vulnerabilities.
“Since becoming aware of these attacks, our team has been working around the clock to develop and release patches that resolve each identified FTA vulnerability, and support our customers affected by this incident,” said Yaron.
At this time, the UC is working with local and federal law enforcement and third-party vendors to further investigate this incident and assess the information that has been compromised. They hope to enforce the law on this issue and stop the release of potentially stolen information.
However, the University advises students to take precautions to protect their personal and financial information. Some ways you can protect your information is by:
Don’t open the links of suspicious emails.
- Many UCLA email accounts received messages stating that their personal data had been compromised and would be released. These emails contained a link to a public website. The University believes that the perpetrators are sending mass emails to create fear among the Bruin community and extort students’ money. Please do not open any messages, especially if the message says, “Your personal data has been stolen and will be published.” Please forward suspicious emails to security@ucla.edu or just delete the message.
Alert your bank.
- Monitor your bank account(s) for suspicious transactions and report any to your bank. Ask the bank for online monitoring and alerts on your account. This will give you early warning of any fraudulent transactions.
Place a security freeze on your credit report by making a request to the three credit bureaus.
Please read the UCNet statement to see other ways on how you can protect your personal information.
The UC Office of the President has also created an email account where members of the UC community can ask questions: communications@ucop.edu. Further, if you receive any suspicious email or phone calls, please report them via security@ucla.edu.
Director of Cybersecurity for Educause, Brian Kelly, stated that monitoring the dark web is part of most universities’ regular security operations. As the university works to figure out the extent of the breach, please do not click on any links, do not reply to any emails or suspicious phone calls, and report anything suspicious to the emails above.
Rachel Kim is a writer for the LA Vanguard’s court watch and city news desk. Originally from Los Angeles, she currently attends UCLA as a Sociology major and hopes to bring light to injustices in our court system and show the important events that are going on throughout LA County.
To sign up for our new newsletter – Everyday Injustice – https://tinyurl.com/yyultcf9
Support our work – to become a sustaining at $5 – $10- $25 per month hit the link:




